What is Secure Access Service Edge (SASE)?
SASE is a cloud-based security model designed to support the dynamic, secure access needs of today’s hybrid organizations, that combines network, connectivity and security functions, offered as a service by the SASE provider.
Conceptually, SASE integrates VPN and SD-WAN (Software-Defined Wide Area Network) capabilities with cloud native security features such as: secure Web gateways (SWG), cloud access security brokers (CASB), state-of-the-art Firewall (NGFW) and Zero Trust network access (ZTNA).
The term SASE was first described by Gartner in a report on August 2019 called, “The Future of Network Security in the Cloud.” Gartner notes that in the SASE market trend report, "Customer demands for simplicity, scalability, flexibility, low latency, and pervasive security force convergence of the WAN edge and network security markets.”
Why is SASE necessary?
The traditional function of the WAN network was to connect branches or remote locations to applications hosted in the data center, ensuring connectivity with dedicated MPLS circuits that ensure reliable connectivity and an adequate level of security.
The increasing deployment of Cloud and Saas (Software-as-a-Service), Iaas (Infrastructure-as-a-Service) and Paas (Platform-as-a-Service) have inverted access requirements, with more users, devices, applications, services and data located outside an enterprise than inside. This makes the WAN network inadequate, expensive and unable to guarantee the levels of dynamism, speed, performance, security and access control required by modern applications.
Therefore, the SASE approach represents the logical evolution of security needs and technological trends and addresses to these needs, by providing network and connectivity security controls at the edge, i.e., as close as possible to the users.
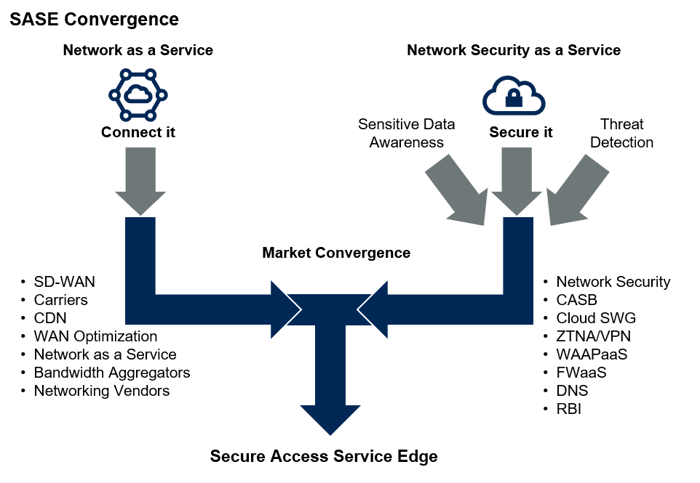
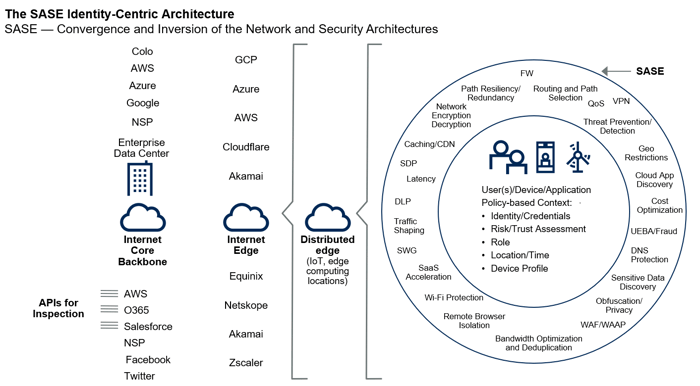
Figure 1 – CDN: content delivery network; RBI: remote browser isolation; WAAPaaS: web application and API protection as a service.
Components of SASE model
The SASE model is based on access security, transforming the network model from "hub and spoke", where access to Internet applications and resources is Data Center-Centric, to "user centric", where access decisions are Identity-centric and applied to the endpoint. The user is identified at the time of connection and on this basis access policies are applied that are no longer bound/limited to the internal or external connection to the corporate network.
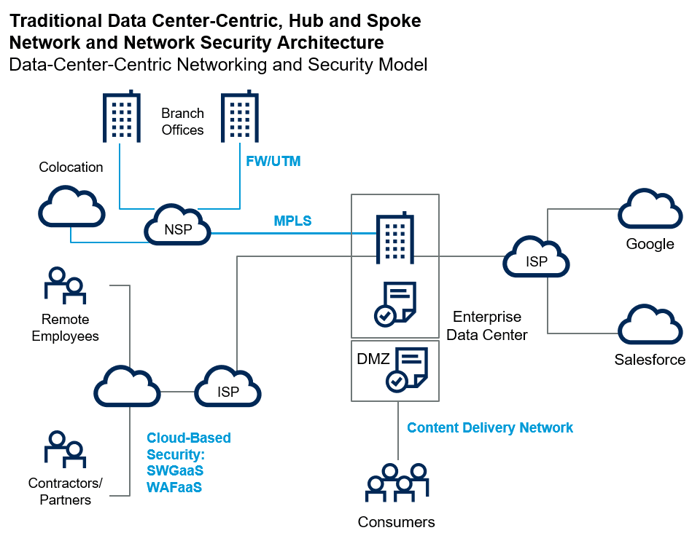
Figure 2 – NSP: network service provider
The main components of the SASE model are:
Software Defined WAN (SD-WAN): a technological approach that decouples network hardware from its control mechanism. It implies the possibility of creating hybrid networks (on intelligent and dynamic platforms) that allow multiple access technologies, bandwith on demand, dynamic routing and security services, integrated with each other.
Zero Trust Network Access (ZTNA): a network security model that verifies users' identities and establishes device trust before granting them access to authorised applications. It helps organisations prevent unauthorised access, contain breaches, and limit an attacker's lateral movement on your network.
Firewall-as-a-Service (FWaaS): a Cloud platform that makes firewall service and security services available everywhere.
Secure Web Gateway (SWG): Web access gateway which integrates advanced security features to protect your users/workstations using Internet resources. Organizations can secure and enable corporate resources while securing and delivering their sites, applications, and APIs.
Cloud Access Security Broker (CASB): Application for the use of Saas applications. In-line implementation for real-time control of Saas User-Application interaction, or off-line implementation based on "API telemetry" available with Saas Providers.
Figura 3 – AWS: Amazon Web Services; DLP: Data Loss Prevention; GCP: Google Cloud Platform; O365: Office 365; SDP: service delivery platform; UEBA: user and entity behavior analytics
Benefits of SASE
The SASE security model can help your organization in several ways:
✔️ Optimized connectivity- Independence from transport mechanism and network equipment
- Active-active hybrid connections for all network scenarios
- Dynamic routing on all available connections
- Uniform extension of the WAN to multi-cloud systems
✔️ Cost saving
- Replace or combine the use of expensive MPLS routes with cheaper and more flexible Broadband (DSL, LTE, 4G, 5G, etc.)
✔️ Better User Experience
- Application traffic with dynamic routing to ensure better performance for critical applications
✔️ Maggiore sicurezza
- Centralized Policies based on the Zero Trust model and customization
- Real-time access monitoring and control
- Secure traffic in Internet and Cloud connections
- Security deployment in remote endpoints
✔️ Centralized and simplified application management
- Centralized monitoring and management dashboard
- Zero-touch provisioning on all functional components
What are the new challenges in SASE Security?
In a context of growing adoption of cloud-based services, sharing information, data and files is becoming increasingly easy and frequent.
Organisations should review threat vectors to adapt the desired safety posture:
- Identification and control of compromised accounts: ability based on user behavioural analysis (UBA) capabilities to mitigate damage caused by misuse of the cloud by employees and compromised accounts.
- Anti-malware automation for cloud apps: a feature that automatically scans and fixes malware infections in the user’s cloud application accounts.
- Advanced Threat Defense: Provides an advanced level of threat protection (Advanced Threat Protection) to analyze files moving in and out of Cloud accounts.
- Mitigation of attacks through cloud-based email: email uses the SMTP protocol, which is a different channel than most Internet access and requires specially designed threat prevention capabilities. The solution must protect against phishing attacks with Isolation (RBI) techniques and, when e-mails contain attachments or URL links, they must be scanned with anti-malware engines and analyzed in sandboxes.
SASE and Kirey Group
Kirey Group supports companies to ensure adequate protection of business information through the adoption of a unique, consistent and standardised approach.- Analysis of AS-IS Security capabilities;
- update of the grid segregation model;
- definition of TO-BE Security capabilities;
- support in the definition and implementation of the Information Security Management System (SGSI) consisting of principles, rules, requirements, methodologies, controls and security measures with the aim of preserving the security of company information and assets;
- protection, in terms of confidentiality, integrity, availability, verifiability;
- definition of appropriate criteria, management methods and use in accordance with the rules of law and internal and external regulations;
- IT risk reduction through appropriate accident prevention and mitigation measures, in line with the IT risk appetite defined at company level.
Our Value
- Specific expertise in Network and Enpoint Security, Threat Management, Data Security, IT Governance Risk and Compliance;
- Experience in security projects;
- Unique proposal.