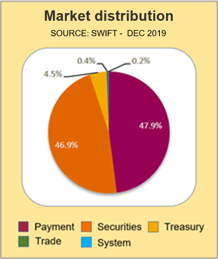
The Society for Worldwide Interbank Financial Telecommunication, better known as SWIFT, globally determines common processes and standards for financial transactions.
By Angelo Chiarot – Senior Security Advisor of Kirey Group
The Society for Worldwide Interbank Financial Telecommunication, better known as SWIFT, is an organization founded in Brussels in 1973 with the aim of establishing common processes and standards for financial transactions worldwide. Used for the exchange of 37.7 million daily messages in 2020 [1], with a growth of 10.3% compared to 2019[2], the SWIFT circuit counts in February 2021 the membership of more than 11,000 global institutions connected by 200 different countries[3].
|
In relation to the continuous occurrence and evolution of fraud events that have an impact on the financial sector (as reported by ENISA - European Union Agency for Cybersecurity and CLUSIT - Italian Association for Information Security) the model defined by SWIFT is the answer to the requests of international banking and financial institutions. The latter had and still have the necessity to arrange a system that allows the monetary exchange from one country to another with certain, reliable and especially secure methods. |
Source: SWIFT, December 2019 |
Initially set up and managed by banking institutions as a replacement for TELEX, now obsolete and lacking sufficient security guarantees, the SWIFT circuit is now the reference standard for the exchange of financial messages. It is also accessible to other financial operators, such as brokers, stock exchange operators, clearing and depository institutions, institutions authorised to exchange securities. The circuit provides for the assignment to the member parts of a Bank Identifier Code - BIC, i.e. a code with a length of eight or eleven characters, uniquely assigned to each associated entity.
The SWIFT model, together with the transactional mechanisms that are based on the exchange of messaging compliant with ISO 15022[4] and ISO 20022[5] standards, is composed of security measures qualified in the Customer Security Programme and detailed in the Customer Security Framework (two of the main technical-regulatory documents on security controls). These measures are designed to guarantee the confidentiality and the integrity of information and the availability of the service, with the aim of mitigating the risk of incurring fraud. In order to guarantee proper levels of security throughout the circuit, member entities must formally and periodically demonstrate that they have arrange, applied and maintained the necessary security controls, according to the reference architectures.
Architectures of reference
With the goal of determining the system components concerned, in addition to the organizational aspects (e.g. company or third party roles involved), within the perimeter on which insists the application of security controls (secure zones), SWIFT requires entities to identify which of the five reference architectures (see Figure 1) is closer to what is deployed in their operating environment for message transmission and reception.
In accordance with an approach based on the identification and mitigation of risk, the identification of the reference architecture allows the timely determination of the security controls applicable to the secure zone and to the internal and external parties involved (e.g. service provider). Elements on which the following Assessment activity, necessary to demonstrate security compliance and maturity. Achieving and being able to demonstrate compliance, as well as being factors that allow the mitigation of fraud and direct loss phenomena, allow the sharing with its national and international partners of the character of reliability and security achieved, thus further strengthening the Organization’s image and reputation.
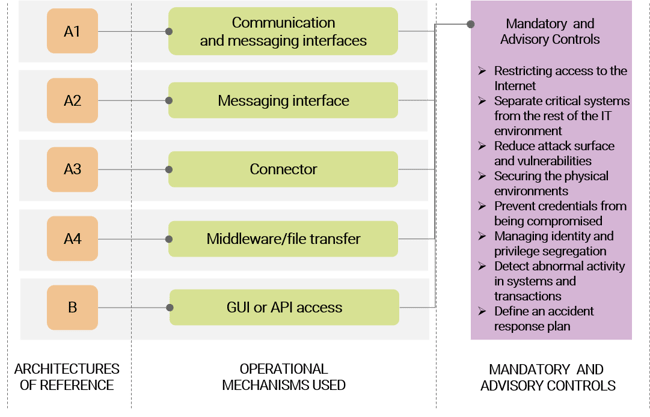
Figure 1 – Reference architectures
With the Customer Security Programme (CSP), SWIFT classifies reference architectures through the identification of interfaces, applications and tools, specifying how different implementations can however be characterized by a substantial level of customization, compared to the groups identified below:
A1 architecture: ownership of license and use of the communication interface and the messaging interface, or of the communication interface only, which typically reside within the premises of the Organization or at the service provider.
Architecture A2: ownership of license and use of the messaging interface only, located at the Organization or at a service provider.
A4 architecture: use of a custom connector, typically using an application solution (e.g. file transfer or middleware such as IBM MQ Server) that allows communication with a service provider.
Architecture B: no specific infrastructure components. The messaging service is used via a PC or other device through a Graphical User Interface (GUI) or through a back-office application through the Application Programming Interface (API) that connects to services provided by a service provider.
How does SWIFT ensure security controls for payment processes and technological components?
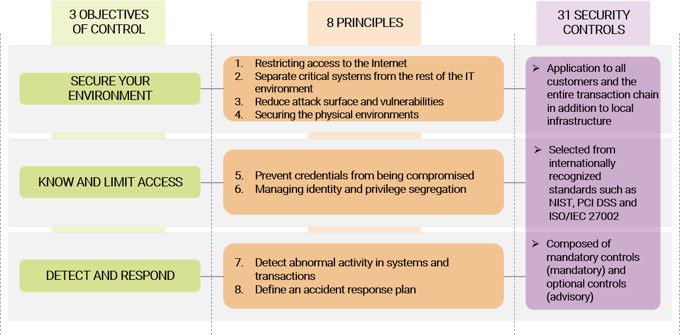
The Customer Security Programme (CSP) also requires each entity to define, document, apply and verify its payment processes and technological components with respect to control objectives, the principles and individual security controls defined by SWIFT (see Figure 2), in compliance with the applicability criteria of each type of architecture used.
The security controls, not limited to technologies but also applicable to persons and processes of the Organization, are divided into mandatory (mandatory) and advisory (discretionary). These represent the selection made by SWIFT of controls from the main standards and best practices, more used and recognized globally, such as the Payment Card Industry Data Security Standard (PCI DSS), Information Security Management Systems (ISO/IEC 27002) and the National Institute of Standards and Technology (NIST), for the protection of confidentiality, integrity and availability of information and continuity of service.
Figure 2 – Taxonomy of controls
What are the potential events that security controls help prevent in financial transactions?
The selected controls help Organizations to mitigate security risks that seem increasingly looming, in today's threat landscape. Addressing these risks adequately thus enables the prevention and reduction of potential adverse, fraudulent and potential loss events, such as:
- Unauthorised transmission and/or modification of financial transactions
- Receipt and processing of altered or unauthorised transactions
- Conduct of transactions with unauthorised/unintended parties
- Breach of confidentiality and integrity of information concerning personnel, business and technological components
- The resulting occurrence of losses related to corporate risk, such as financial, legal, regulatory and image risks.
The Regulation requires that organizations must certify annually their compliance status, typically within the period July-December, in relation to the annual update criteria of the reference documentation, in particular the Customer Security Control Framework (CSCF).
Starting from mid-2021, the attestations of compliance submitted in accordance with CSCF v.2021, shall be the result of the safety control assessment conducted independently, exclusively through:
- Independent internal assessment: conducted by functions belonging to the second or third line of defence[6], such as compliance, risk management or internal audit or their equivalent. The selected function must be independent from the first line of defence and be in possession of recent and relevant experiences for the performance of Assessment related to cyber security controls.
- Independent External Assessment: conducted by an independent external organisation with relevant expertise in cyber security assessment and certified by the security industry.
Kima's Accreditation as SWIFT Assessor and Compliance Expert
Kima Projects & Services S.r.l. | Kirey Group, already Certification Body for electronic payment environments since 2006 according to the Payment Card Industry Data Security Standard (PCI DSS) in banking and finance, in 2020 has obtained accreditation as an Assessor qualified by SWIFT, through the Customer Security Programme (CSP) Assessment Provider, enabling the evaluation and validation of SWIFT payment environments.
Kima has a Senior Security Advisor with more than twenty years of expertise and experience, as well as security certifications that allow them to be qualified as suitable entities for carrying out compliance activities regarding the security requirements of SWIFT.
To date, the certifications held by the Security Advisory Team are the following:
- Payment Card Industry Data Security Standard - Qualified Security Assessor (PCI DSS QSA)
- Payment Card Industry Data Security Standard Professional (PCIP)
- Certified Information Systems Auditor (CISA)
- Certified Information Security Manager (CISM)
- Certified in Risk and Information Systems (CRISC)
- Cybersecurity Nexus Fundamentals (CSX)
- Lead Auditor ISO/IEC 27001
- Internal Auditor ISO/IEC 20000
Actively involved in the provision of services for banking institutions and financial operators, Kima is therefore the appropriate interlocutor who has an offer for the SWIFT Regulation which consists of the following main activities:
- Identification of the customer’s reference architecture (A1, A2, A3, A4 and B)
- Definition of system components and parts in scope
- Conduct of preliminary conformity assessments (Gap Analysis)
- Performance of mandated technological audits (Vulnerability Assessment and Penetration Test)
- Formal assessment and validation of compliance for the purpose of periodic assessment
- Staff training
Notes
[4] ISO 15022 Securities - Scheme for Messages (Data Field Dictionary), Part 1 - Data Field and Message Design Rules and Guidelines e Part 2 - Maintenance of the Data Field Dictionary and Catalogue of Messages, ISO.org
[5] ISO 20022 – Universal financial industry message scheme, ISO.org
[6] Bank of International Settlements – BIS, Occasional paper n.11 - 2015, The four lines of defence model for financial institutions